What's DMZ Network?
DMZ stands for Demilitarized Zone. It's a network security concept that creates a buffer between a public network (like the internet) and a private network. It helps to keep your network secure and protects your important information
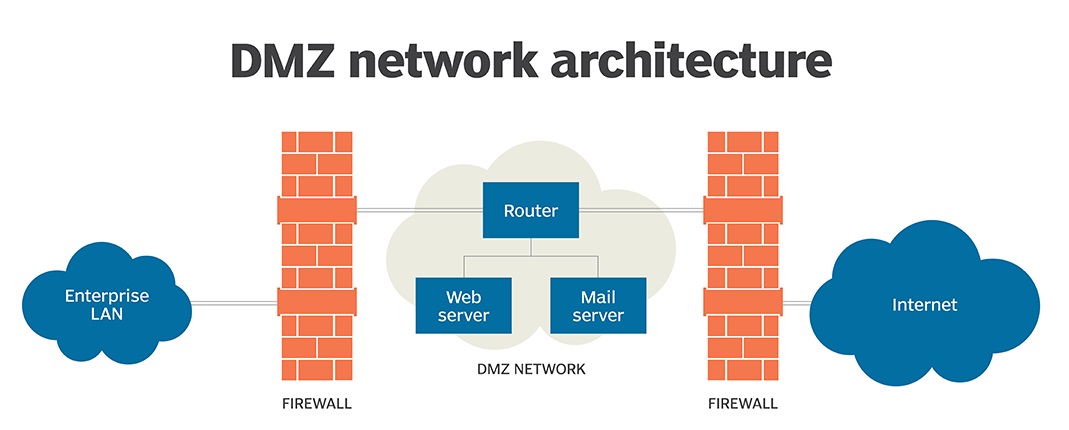
DMZ: A Simple Explanation
Imagine a castle surrounded by a moat. The moat is a barrier that separates the castle from the outside world. It keeps intruders out and protects the people inside. A DMZ (Demilitarized Zone) is like a moat for your computer network. It's a buffer between your private network (like your home or office network) and the public internet.
Also, You can thnik of the DMZ as a gatehouse. It checks people before they enter the castle. Only those who are allowed can pass through. In simple terms, a DMZ is a safe space between your private network and the public internet. It helps to keep your network secure and protects your important information.

Key characteristics of a DMZ:
- Isolation: It isolates systems exposed to the public network, reducing the risk of a breach affecting the entire private network.
- Controlled access: Only specific services and systems are allowed to operate within the DMZ, minimizing the attack surface.
- Security measures: DMZs often have strict security controls, such as firewalls, intrusion detection systems, and regular security audits.
Common examples of systems placed in DMZs include:
- Web servers: Servers that host websites are often placed in DMZs to allow public access while protecting the internal network.
- Mail servers: Email servers can be located in DMZs to enable communication with external networks.
- VPN servers: VPN servers may be placed in DMZs to provide secure remote access to the private network.
By using a DMZ, organizations can create a more secure environment by limiting the exposure of their internal systems to the public internet.
See Also